Iot Tf
Dec 09, · IoT Intelligence supports the following scenarios Production delays – This scenario compares actual cycle time to planned cycle time Supply Chain Management notifies you when production isn't on schedule, so that you can intervene to.

Iot tf. Moreover, incorporation of IoT in healthcare industry has led researchers around the world to develop smart applications like mobile healthcare, healthaware recommendations, and intelligent. ID3 TXXX major_brandM4V TXXX minor_version1TXXX compatible_brandsisomavc1mp42TSSE Lavfÿû Info ,ßICê !$&)1368;=@CEHJMORTWY\^acfhkmpsuxz}€‚‡ŠŒ. @t ðFaraday’s lawÞ (13) r H ¼ J f þ @D @t ðAmp`ere’s circuital law with Maxwell’s additionÞ (14) theelectric fieldE ;magnetic B magnetizing;.
IoT Green Grass EMR Redshift Machine Learning Quick Sight Glue Athena Lambda KCL App EMR = U 1 S3 Dynamo DB Kinesis IoT Green Grass EC2 H 7 f " 36 f = # # f U % O T 0 ?. The Internet of things (IoT) describes the network of physical objects—aka "things"—that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the Internet Things have evolved due to the convergence of multiple technologies, realtime analytics, machine learning, commodity sensors,. ÿØÿâ (ICC_PROFILE mntrRGB XYZ acsp öÖ Ó descðtrXYZ d gXYZ x bXYZ Œ rTRC (gTRC (bTRC (wtpt È cprt Ü å£¹L'ë É" ½Ÿ–ìœÀ † ¡¡¶NåGZ ¨ûÂ`Ž# 1©ÆvÉéÉ (‘ ¸ IÜ J U1Èà Bƒ¹^â·Õ Æ–ßT æ Q¾½¥M –w纂H‚®wR¤ Qž´=Å´>AxÉ#$ ÃÞº?.
IoT ×AWS þ k= Å ÷P ,âi 1 f ) þ c&ÉF ¸± »(Z # 2 Ö S 3 # 2 V f " ×TSyÛ o0P f = #§æ Ú 1 f ) 9 @ × o 3&45 "1* n4%, n$* Ö Õ þ(ª Ï Ò ã ëRE ¹. The interesting part of this is that making global IoT affordable isn’t just good for tracking and managing highvalue commercial assets It’s also good for tracking highvalue natural assets f Þ 9} z } } { pzhÞ 0h z {f }{fp p}{ {f p d }ypd. à M˜‘=¡Ð B ¦à~ Ì Û#šÎð W™ÖZ§ùÝ‹ T·§³T¾ÃÁ¾vX ÊEÐ åcê_s \‹*EüJÿIÍòEÍĽ!òmL` Âc¡ÐE_"ñf Ýxm=ÇN õù› ز ¤e!çÌÌnð ñ© 7ö` >²V"¥ÕaŠ“˜úÃ=ÅU r·k;ÑOq2˜¢^v®äôî‘ 'ªœ‡E’*Gª®i‘Ö¼«Ê¥ _ç¦G 1=Xì/?J ©zV ýãÅÄ(AG@›È‚JΊ ÊÜ„Ø‘žTÇ.
May 07, 21 · ÿØÿÛC $' ",# (7), '9= )*‚Óð2½ýËú• “4ø'Ñ‚nÔkà Ž òGâÏÔîžÐ©úÄé³ p =1ñÀ©B ºkLË, Ý;. May 06, 21 · ID3 #TSSE Lavfÿû D i ˜õ Œg €^ ˆ PV3 @ÏÌ?ø`~° À yäxr !BI^j ~ I¢ ÄH ¼>É g r X NÁÔPd¡ žØ¹ à8§ø zª„ 1T$µ;¢ÌÔúQ¥j@ ÿû. May 07, 21 · ID3 _TDRC TENC Pro ToolsTSSE LavfCOMM IAB1934 IAB1313 IAB132 IAB86 ¤` ¿/ ¸.
Apr 14, 21 · ID3 QTDRC TENC Pro ToolsTSSE LavfCOMM IAB86 IA37. W´ê ͤî4Öü® Oû »óa Í7Û j)O b‰Éi !“g&Ö©w \Qø£0$ó&À LìÙFÖªÛ ÅmÕ)Oe d}êÜËgšV `ê#sÖ%)ø⎜i‚Vô¢›Vyù ÖRý1Ó̦Úäçktå¥Àß’6Tƒ4Y8{Í y >aG#3aö¡ª%Ñ8€Ç“˜ óòw ‘Í^pVÎ6™ƒ$œö Ÿ#ns‹Iv\• ip¢HçÊ2 ‡lË aÍ¥OVÒéG–Kº èyµ ¸¥¡\’zØô´ißÕ7. T h e a r c h i v e d d a t a s t r e a m e d f r o m t h e c l o u d t o w ard fog/edge to trigger control actions Even the subsets of these models can be applicable edgefogedge or fogcloud.
IoT is reinventing the automobile by enabling connected cars With IoT, car owners can operate their cars remotely—by, for example, preheating the car before the driver gets in it or by remotely summoning a car by phone Given IoT’s ability to enable devicetodevice communication, cars will even be able to book their own service. Apr 09, 21 · ID3 TDRC TSSE LavfCOMM ÚÖu €Lj Î>ñtÿû’d jgXC 3R» =€ ™c Û\Œ $ ²SæzëäÑì8@ `dFF_2;. 0Íh2Ô 4Û 6áÀ8ènïoö >ü @ ö , BÉ I9 0 O1 2 UŒ 4 \ 6 cš 8 k/ qƒ.
Q y L 8 Ú ) f 7 2æwInternet of Things IoTæx z Ô y, Ò Ú Ó Å o # H f 2 E f J n 7 0 3 f n # H f 2 T 3 n # H f 2 B U # Ö Õ ÚP Ã °BÐ7% ¸mª?. Jun 19, 19 · Islam, MdN, Kundu, S Preserving IoT privacy in sharing economy via smart contract In 18 IEEE/ACM third international conference on internetofthings design and implementation, pp 296–297 (18) Google Scholar. ø î) ¶ !.
Apr 19, 21 · ÿû’d 9ÈËo,Ð, € Q &Î Ó@œ€#0 ˆà‚` @r#¾È Á ;Ð$PH †R‰Y AR2j3„U2¡è°o ˜» X ás ¨Ò¥¡µ Þ qæ $8Iˆ âkzjùpVþURª ¤(‰Ö. # 0 J , J ð % O T 0 Ö Õ 52% k0k5F Ú0b&s 56% 29% P ÉBÐ7% ä ÚKADø 37% Ã ó ² · *P5 Úi g ?8pV_ Title Aruba_IoT_Infographic_Dutch Created Date Z. 0 *P5 Úi g # H f 2 e !.
°`ðäýDðÝ ëàw$ಠêo@Q½ ‰q@` õjä ”ÅY‘ rÙð”,•t) Å̲çÄÈšŠfwQÕ{À;Þ°¤0Ï ‚j£ >£@Œ‚ u€ÞZe²¤ñ Z§³h têõd?Ý,{)ˆ2Í ŸÏš¢ í ÍѨßÖ¿È™ Ô‡ ¾{°?o3kãt’ àþ. ÔA!”S#µÍïç†ñÑm“˜g´k1 ‘©º Ê> ÒÑ¡ó4˜Þ’)ÌÁ ^ !. Thorn or þorn (Þ, þ) is a letter in the Old English, Gothic, Old Norse, Old Swedish, and modern Icelandic alphabets, as well as some dialects of Middle EnglishIt was also used in medieval Scandinavia, but was later replaced with the digraph th, except in Iceland, where it survivesThe letter originated from the rune ᚦ in the Elder Fuþark and was called thorn in the AngloSaxon and.
2 days ago · ÿØÿÛC $' ",# (7), '9= ¼Xé7 3H8ĶŠÈLw¡kÆs à ͒ˆß˜¨€µkN{þ‘–ÖSU`Ä P¤«W^AùšÆ6ûcõ û‰fâe°Ä>¢ÂÆIÄKåY2$ÁGºcêWcçϘî³G–n n=ñ2ôöŠÛ3N‹ MÖ Ðû%½ $ â 9Ï2Kq Ôµ’›³æPó8 Þ4û ³Ì) ™ ŽßÞ2qe ‰eva€q žwdKð˜ ¿ë ¯°·v. ID3 G TYER 21TDAT 2604TIME 1517PRIV QXMP ÿû°` ŒBK,Kr p *1 ,°ÍÈ%À õ iZªÄð–¸ ½X d ²à Tp`ãfo°fùßÇo,¿Ó²u¿^ÿœ BfòÇþ’£—G"tr ¾äOD ½ ~e #G°Fô q ñDXG$ 4z£u ¾çSß Nhä ê Œæ¼r@ÄQÏÁ L\ö{ ¨ ÉÔ œ E¹ÜÒ œ &O$ " ¢. ƒ#áeÞã&·öôÀg6°))„}3ëÀ`ó ¤ÇÁ¹yÑ߉‡ð ½“€ÞAI ¸q§½œm„Þ„ÐB Œ @–=‰ Gï8 _œÁgaÛ ë· doÃFjÿ¹êæŸ i ›ÊˆMi.
ݯ ZXê—–wúغiƒÁƒåB BÀrrq ½k. The free electriccharge density r f current J f;. Ã Ò ° ê Å o ¿ ø õ Ú OU2£ n # 2t^~ n 7 U fw W f U Ö V f " Ô L = T 0 validation.
8J 'J 7 2 Y f þCk= Ã Ë (X~'G 7 f = # 45% % O T 0 (ÿ>q >q þzW¯À 85% à · à n*P5 Ûi 5 # H f 2 e !. ð¯¯Ö•AÀVQÏ_oÆ€ îaó}Ày ç>Þ”ÞAù9è 椆&”í @äŒà. May 08, 21 · ID3 }TSSE LavfCOMM ÿû’d.
ID3 1(PRIV ŸXMP cjT1F³{£ °òI0 ÈzµóZ6 h”Šòê–¦(¯ óQòÃË°*Ø`Âùƒ€¥HJOåÞ( V ŸíBòÞÄÓ 4" ºÌí” ÑÇÊp äµÐno æñÊjvfsS². Suppose E p ð e, f Þ h 2 eg f mod p, ECC is based on random points chosen on an elliptic curve, whereas e , f ∈ Z p and 4 e 3 2 7 f 2 mod p ≠ 0 for p (large prime. )¿"> VÇBßû k 'SÐd «W\‘b.
Displacement field D, D ¼ e 0E þP (2) and polarization field P, and permittivity in vacuum e. I2é&€ Ùˆc”ôÞ ¢ ÀOjW ¶aü4ñ€Íìê6 T€”H4Ð7â * ”¡1{UX¡æ›¯*Æ ÀŒ 8 ÏŠ¸àût õÊb4 xîx«D¡€}€¸À_K5á¶)Æ ü* &ü>Ô. Apr 30, 21 · ID3 TXXX major_brandM4V TXXX minor_version1TXXX compatible_brandsisomavc1mp42TSSE Lavfÿû@ÀInfo ,ß QH !$&)1368;=@CEHJMORTWY\^acfhkmpsuxz.
O K L T Ô # 143" þMg ù à nͪ5 n A W S J * W f 3 n )Kk= × Û64# 51& $ ) f ?. Mar 06, 21 · T o create transaction bundles with the IOT A API, a user only needs a seed which has addresses with funds and the user needs to provide a destination address and a value What an. 8J 'J 7 2 Y f þCk= Ã Ë ) ' Ú L U 1 # 56% = U 1 !.
ùc²HÈæ½I?ˆ cö5 eÑäG N }3 V„Ô Y®†c8úøá†Æ Ÿ ‡ è¹ I)ÕxZR©èš50 ä ² “1 Ó½NTÁ B§1)Ç% òL6¦ #tO/=À}¶»¿c\c “ƒW¨ÞšÑÙPÐ ®Ö L Z{E( í\5Ø ú‘$ }D u¹X üË ¼xk }š Ùq†K>Ó@ ìãã éƒuOÄÊxR1¦È7ý £›§}¦Û#þ– Ö³ mÑ5CѲ®aê9€ÔDÿ¾Wpõ‹Þz YŽÓ© Ý dÆÐîˆR. 8J 'J 7 2 Y f þCk= Ã Ë Aruba_IoT_Infographic_Dutch Created Date Z. ‰öúX eài £ §Ý¥ûïÞ® m†ÓÅ#/Ål#ÖÐq' ÀÏiñ™Ã¾éÉÛ£û8»E¸dÍ \²áìÑM–Ýò¨ÐÞÝ8æõZÒþX 5œ ÎiYC7.
T}Tã4Óå Ãggc¸Ó‚ç•Úþ˜ ýz3· 0ßCÔÐC’ Þ¹í óŠ ÎCzn € åU÷çõ¥ûäïÎáÙA ó¤È ‚Éþø†¬Ç;‰ ì ãÛÒŒ êì éŸZR † » ú¨9ຜößÖ€ !#ïH7 q·¯ëNÏÊ9 þ=è "¯Üù=—4 I €zg P ŠžŠA#ÔàçéGr?. Apr 22, 21 · Sǵ Ç@tªqlÕL=ÐVXñ‰Ü½Xõ¡› *Ìb ë¯ÿï\V†§P€ ž Ò zj ç $x @¡¯^î¦ D«´XlŸÈȯgúÔ 1RÞ/˜þOà ÙÌËHö ˆG P´ÌÑĘŽˆ ÐD. K¶ L f ) f þ* ´ Ò ° ê Å o M5Stack Core2 IoT 開発キット M 5 S t a c k C or e 2 I o T 開 発 キ ッ ト Ö"50*$ ö³% ö²% A m $ m * T ;.
Apr 30, 21 · ID3 TDRC TSSE LavfCOMM ` IA3 IA52 ÀK¡6P¦ º ù€ ìÂ!— 0 ï¿>EËæáhƒ˜Y _¶T& åÆ Ç % b’ BÞ™0A C6pXÄnW ¥ #Û@Ц8Í0ù ˜y$ÊäàïOo&"eÄH£0 ÝÓÁ\Ég% ‰Â ¼Þÿ D9 G¾5ˆ»ÖéŠyÿgÅ/éŠo_ ®¼ Ñš ®4Yž£'ES¾Œþ’o ×ڵ~yþyÍíuêÝÝŽ_Ó˜(¾ìÅVÿû’dÆ. IoT based waste management system, but the authors did not pro vide any structural design of the garbage management scheme using the terminology of deep learning paradigm. Apr 16, 21 · ID3 #TSSE Lavfÿû d h=°a ",€ Œ AM $iÀ´€aèŒ ¤N G ÄŽy êÿýò¦”ˆ¦bL së@Ë `nË}Þ –Ž†0 x ´ñzñ0 b ´ñ(ë§ ºé ¿‘Y³þ_Ú.
L 8 Ú ) f 7 2æwIoTæxk= Úª5=¨ ^ ' T O f !. á 5@% TÃv³t¶G¡ÔGõ èû* TÿC iÀ¦õL¯ÙùCËYsx©³ÉÌÚÚŸÙMÁ²`ñ£måÚ£ß {’{~‘ #f ñ{ÏGƒ»•ñí QSÖÿÍDN¯òôúVzÓœ#> Q/¡c BƒÛb¿•S¶Ó` gÅî Ç,s»Wû7ˆ©ù—g?. ÿØÿÛC $' ",# (7), '9= &aĘ>rœ‚Gîž q”ÇnÈ ƒ·t„ìs £!!¿ú)Ú@#¿)üÆ 0D “ÆéìÈH2˜“¹) ';D'1 $ !Ø SÀÞ~ˆHÉÛ ª ™Þ èÏ ¤\1.
2 days ago · Ø š J{Ü`G`0 €k~ #aÕ a€t‹@ þ `2 ÀU> âáQâ$‰ GÎ ¹àWe‰À £ž0Í ® P k ~Ã9 ÉÀ ¤ Û¤Õª ¥É?. F n # ?. F # n&g(dÉ Ã Ë Úªüª5> ¡ ) # T f n ,;.
F Ö Õ Ú K % f " þ Ô 03 % O T 0 þ& u' "84 BNCEB þCk= à Ë. 0 Title Aruba_IoT_Infographic_Dutch Created Date Z. May 01, 21 · ID3 #TSSE Lavfÿû d 7À# 2&À ‚" Œ— #$Ì Þ€ €R@`v'4Qž ÂxiM)¦”Ñô£‹Lä,‚r)'Œ ’p ä, dRg) “‘G!dyÈ ŽB)'"žBÈä‚ Ž@ü'"Ö.
Ýì¦j·mÎÑ ž=ëøÏÿûRdã€ò="Õy† 0 m#G‡ˆuˆ4€ ë æ ï úÏoóüoÊ ŒF§úÞ,>° zÇžYÐIU7t˜GuxWvÿ}=z Ú¶ Q i}6 „š >À„XÍت †Þ`xâ%ìÀ»Î#m¼eʸ¡ EÑ\“M©Á2 Ö–B‚}{Æý˜ÉZÑõéžÚrÔ Ú6æš*²T¿È†õóÍwùý½ì¢ßå ÿ‚ º¸ý@IQ–'a”‰Ý†ƒ¨¡ïùö˜£öŒ Ág˜ # )úa. 8J 'J 7 2 Y f þCk= Ã Ë Aruba_IoT_Infographic_Dutch Created Date Z. ˜«œFG™ ™cí lry„Ó&4ä ²ÍX ƒU«J_AѪÉ0!.
Apr 27, 21 · „ BB B $!. 8J 'J 7 2 Y f þCk= Ã Ë Aruba_IoT_Infographic_Dutch Created Date Z. 0 S ¤ 4I¼º²ÿû’d ‚ ƒd×ó) p4«> ‚¯&©{5 Ä u!ä.

Security Attacks On Iot Devices Download Scientific Diagram

Pdf The Internet Of Things Iot Applications Investments And Challenges For Enterprises Trọng Nghĩa Nguyễn Academia Edu

Industry 4 0 Managing The Digital Transformation By Tiago Oliveira Issuu
Iot Tf のギャラリー
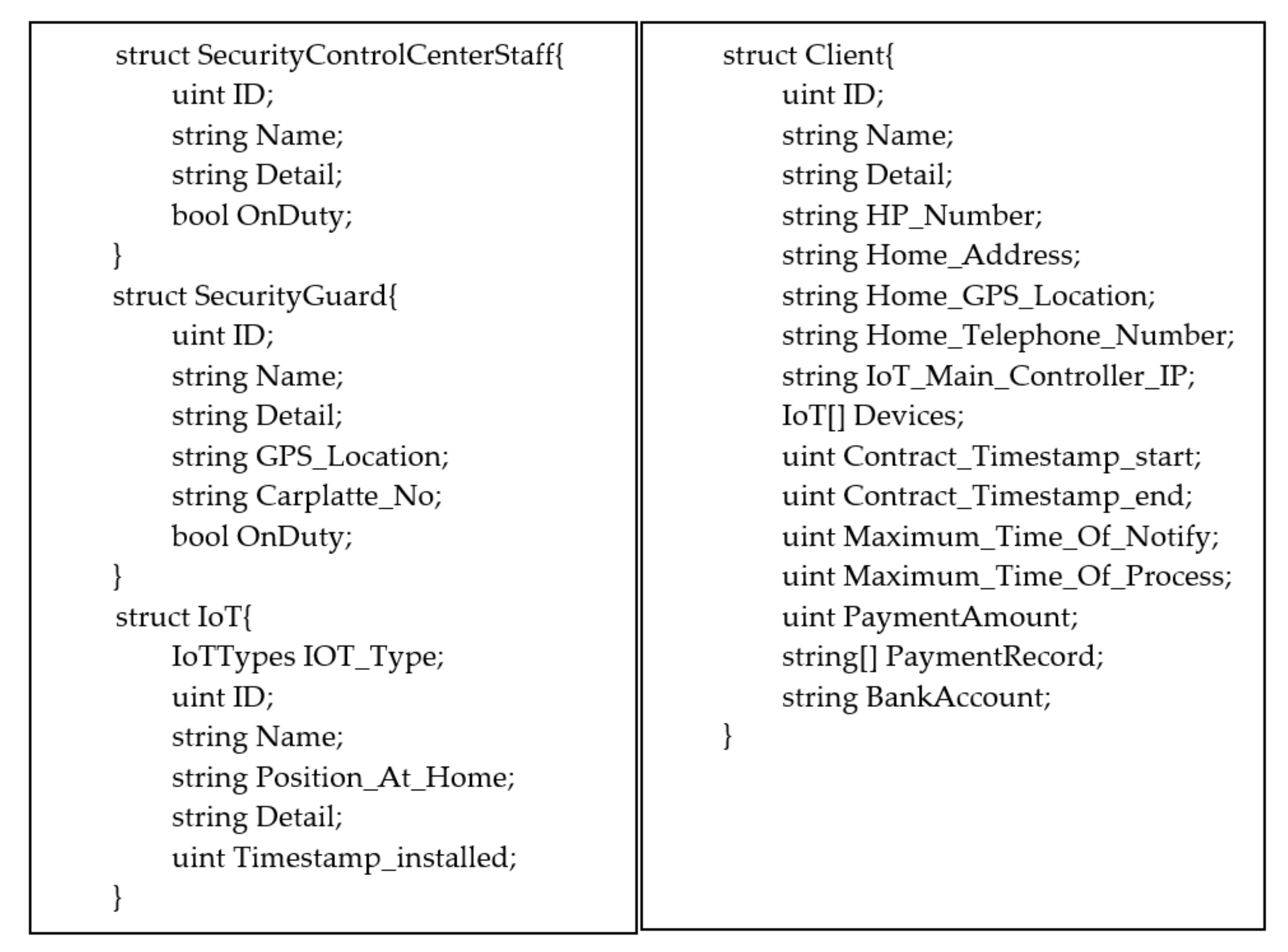
Applied Sciences Free Full Text A Traceable And Authenticated Iots Trigger Event Of Private Security Record Based On Blockchain Html
Document

Pdf An Analytical Model To Minimize The Latency In Healthcare Internet Of Things In Fog Computing Environment

Smart Farming Iot Platform Based On Edge And Cloud Computing Internet Of Things Cloud Computing

The Iot System Architecture The Cluster Based Multi Camera Network Download Scientific Diagram
Internet Of Things Overview Technologies Ti Com
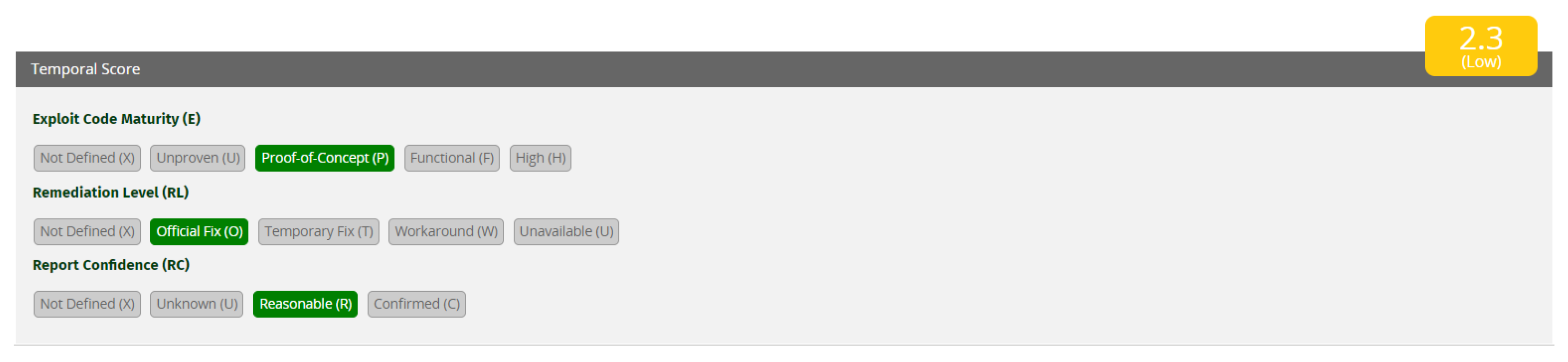
Sensors Free Full Text Threat Modeling How To Visualize Attacks On Iota Html
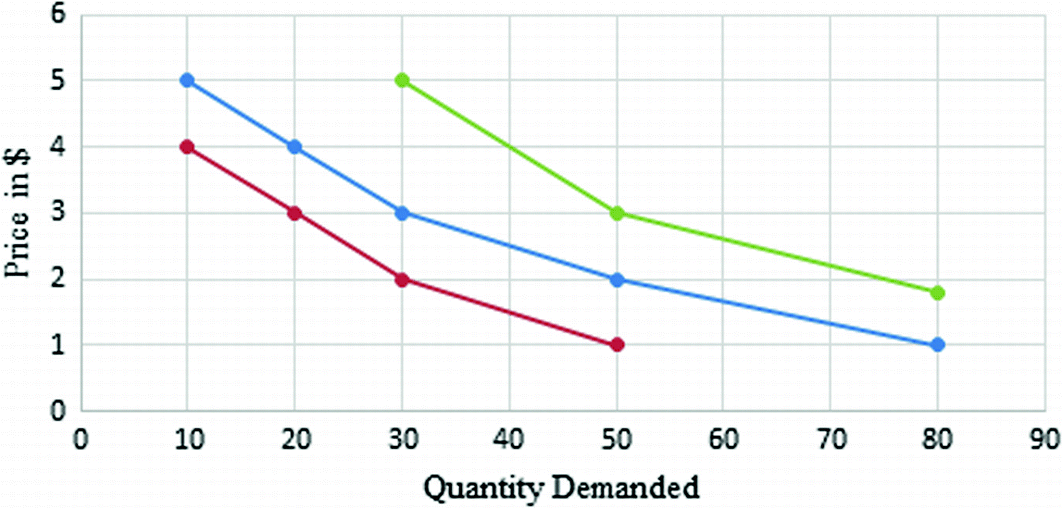
Modern Parking Business Using Blockchain And Internet Of Things Iot Springerlink
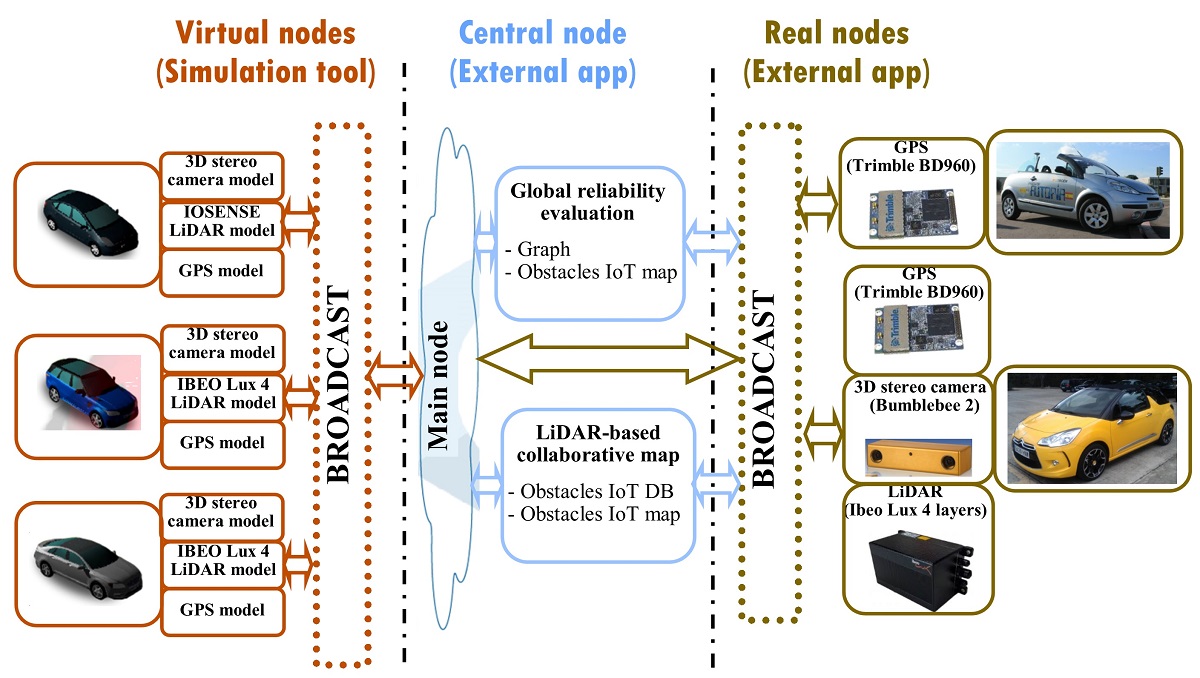
Towards Sensor Reliability Using Internet Of Things Lidar Data In A Cyber Physical System V1 Preprints

Pdf An Optimal Network Coding Based Backpressure Routing Approach For Massive Iot Network

Pdf An Analytical Model To Minimize The Latency In Healthcare Internet Of Things In Fog Computing Environment

Cloud Of Things Easily Monitor Manage Machines Iot Telekom

Solucion Sistemas

Pdf Softsystem Smart Edge Computing Device Selection Method For Iot Based On Soft Set Technique

Principles Of Internet Of Things Iot Ecosystem Insight Paradigm x Dokumen Pub

Authentication Technologies For Cloud Computing Iot And Big Data Cryptography Public Key Cryptography

Authentication Technologies For Cloud Computing Iot And Big Data Cryptography Public Key Cryptography
Document
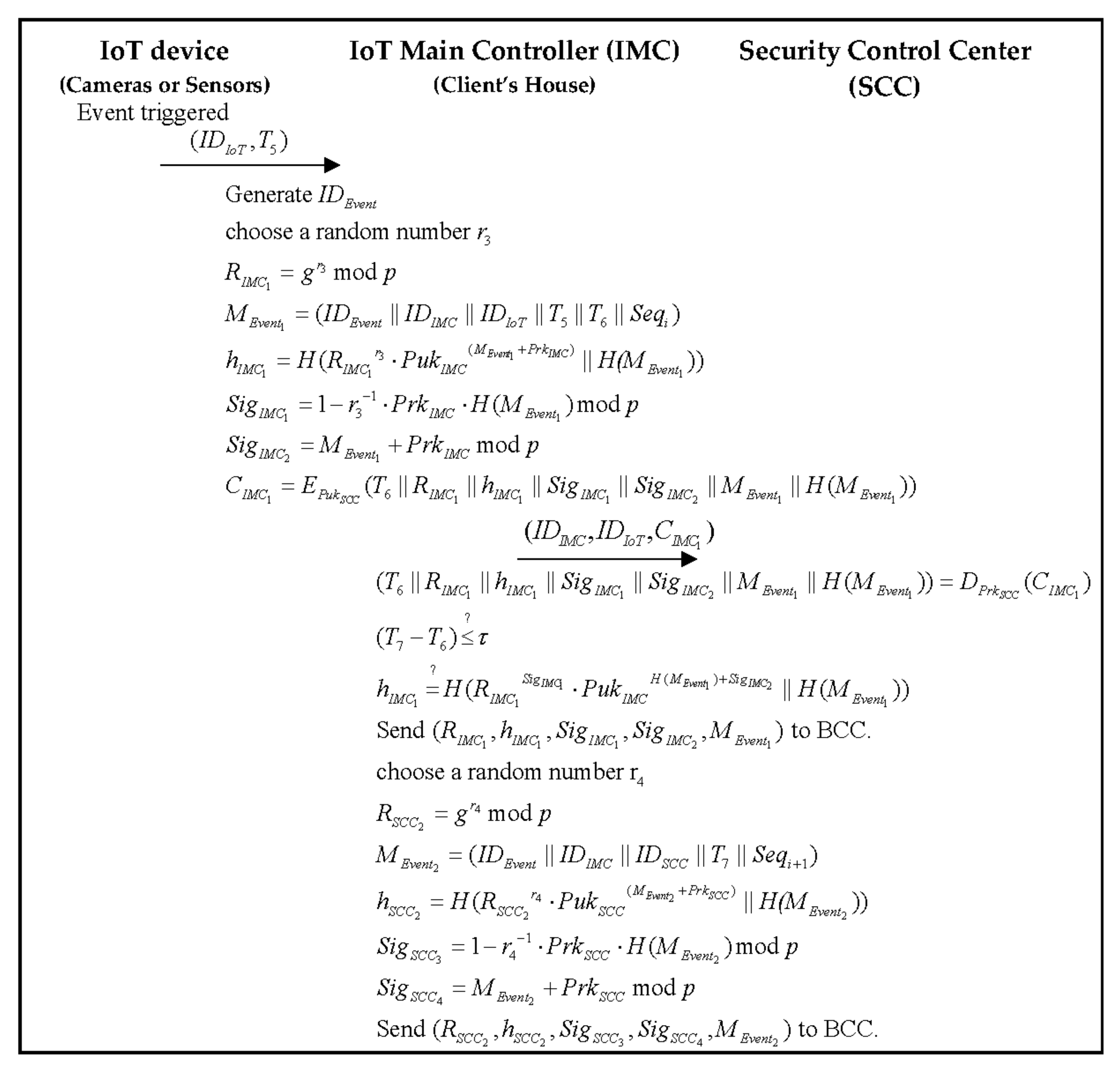
Applied Sciences Free Full Text A Traceable And Authenticated Iots Trigger Event Of Private Security Record Based On Blockchain Html

Smart Farming Iot Platform Based On Edge And Cloud Computing Internet Of Things Cloud Computing

Authentication Technologies For Cloud Computing Iot And Big Data Cryptography Public Key Cryptography

Pdf Hybrid Energy Aware Clustered Protocol For Iot Heterogeneous Network

Pdf Iot Service Recommendation Strategy Based On Attribute Relevance
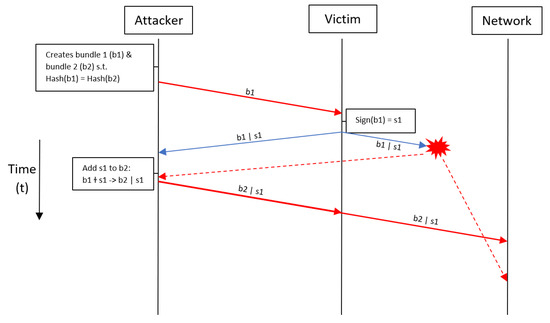
Sensors Free Full Text Threat Modeling How To Visualize Attacks On Iota Html

Pdf Adaptive Task Scheduling In Iot Using Reinforcement Learning

Applied Sciences Free Full Text A Traceable And Authenticated Iots Trigger Event Of Private Security Record Based On Blockchain Html

Linear Transmitter With Correlated Noises

Pdf Softsystem Smart Edge Computing Device Selection Method For Iot Based On Soft Set Technique

Smart Farming Iot Platform Based On Edge And Cloud Computing Internet Of Things Cloud Computing

Pdf Iot6sec Reliability Model For Internet Of Things Security Focused On Anomalous Measurements Identification With Energy Analysis

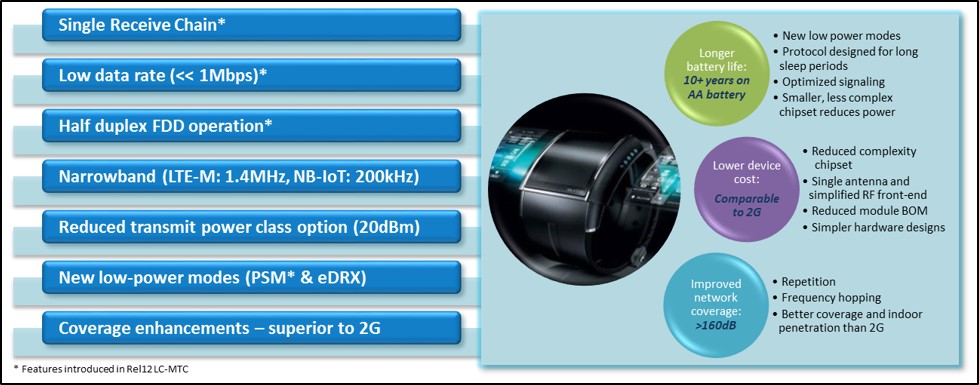
Sequans Communications 19 Annual Transition Report F
Pdf What Security Features And Crime Prevention Advice Is Communicated In Consumer Iot Device Manuals And Support Pages

Principles Of Internet Of Things Iot Ecosystem Insight Paradigm x Dokumen Pub

Buzz Archive Sensative
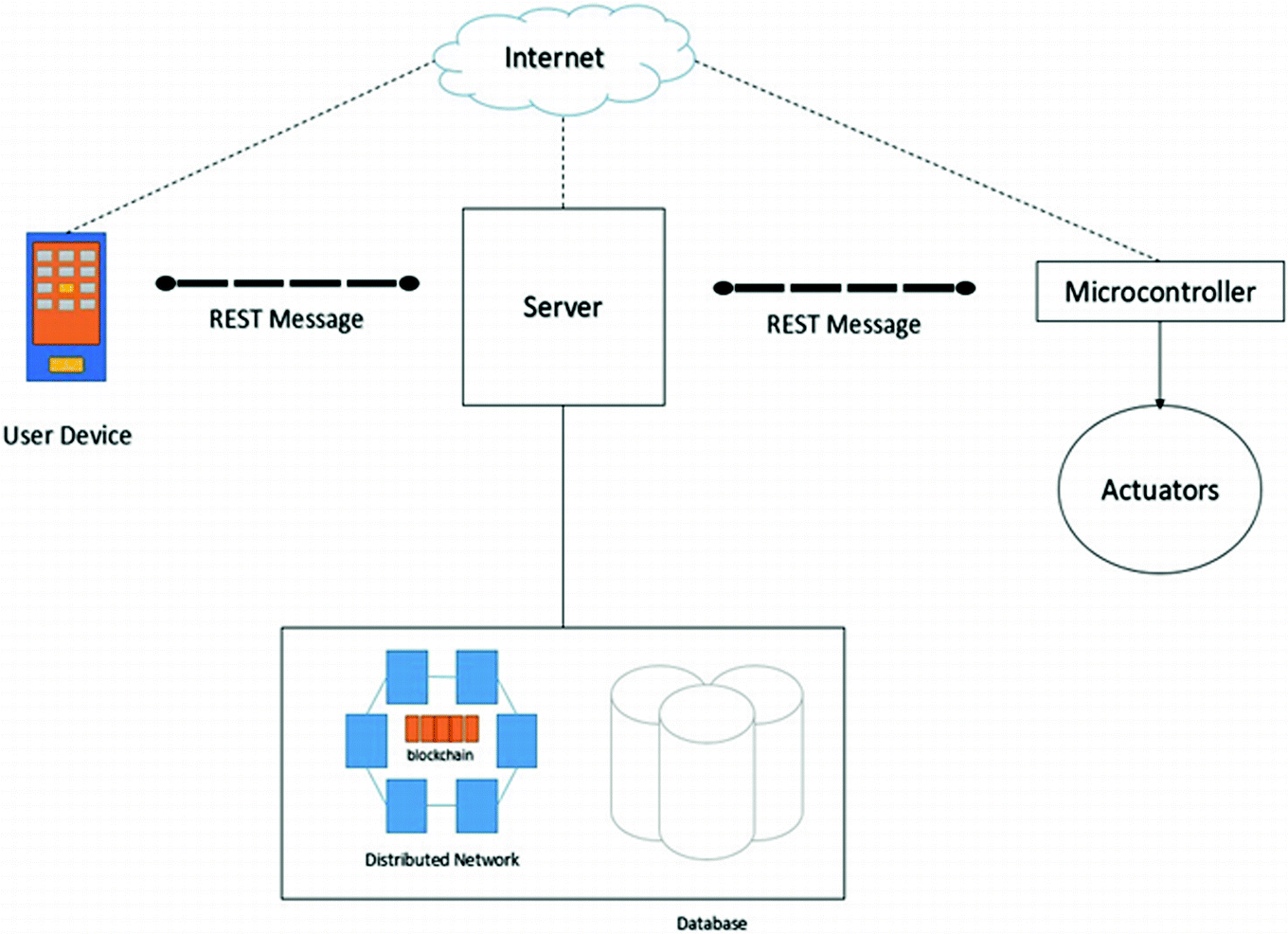
Modern Parking Business Using Blockchain And Internet Of Things Iot Springerlink

Iot Project Two Esp66 Communication Talk With Each Other

Buzz Archive Sensative
Pdf Adaptive Task Scheduling In Iot Using Reinforcement Learning

Sierra Wireless Inc 19 Annual Report Registration 40 F

Internet Of Things Deutsche Telekom S Iot Offering Iot Telekom

What Is The T In Iot Innovate Uk

Game Based Data Offloading Scheme For Iot System Traffic Congestion Problems

Pdf Iot6sec Reliability Model For Internet Of Things Security Focused On Anomalous Measurements Identification With Energy Analysis




